Defining and securing privileged access in modern environments
Simon Moffatt
•
Nov 20, 2025
Simon Moffatt
•
Nov 20, 2025
This is the second of a three-part series looking at modern privileged access management and how its evolution to the protection of more systems and more identities leads to security and productivity improvements. Article 1 discussed why PAM needs to evolve. In this article, I will summarise some of the key capabilities needed to make that a reality.
➔ Risk evolution: static to spectrum
➔ Isolation to integration
➔ Varied deployment landscape
Privileged access management (PAM) has traditionally been plagued by being hyper-focused on specific user groups, systems and protocols. PAM was often handled as a cousin to the broader identity and access management infrastructure consisting of identity providers, single sign on, governance and authorization for the “standard” workforce user.
Whilst traditional PAM often fell under the “CISO budget”, it was tasked with securing access for key IT administrator staff who needed root and configuration access to servers, systems and data management tools.
A decade ago, this view of “high-risk” systems could be centered around on-premises components that could be physically and logically managed by data center access and virtualization. Fast forward to today and high-risk systems and the personnel accessing them have broadened widely.
We see a range of system types (from API-fronted configuration and control planes to cloud service provider infrastructure and dev-centric everything-as-code), all deployed across a range of locations from platform as a service, private containers and SaaS to classic on-premises.
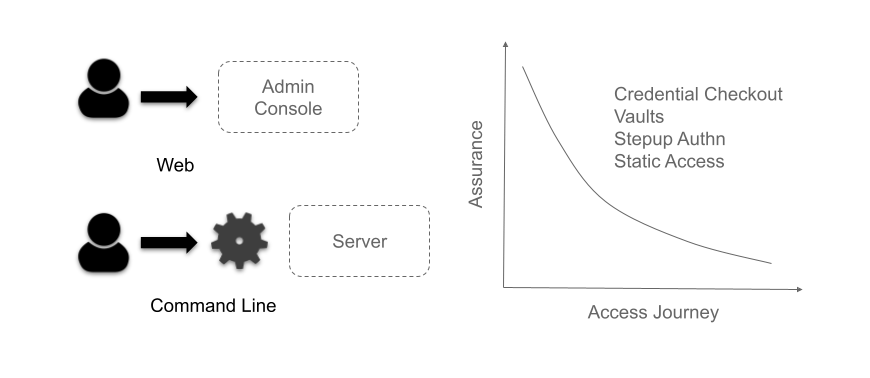
This proliferation of both systems and users accessing this mesh of high-risk resources can no longer be managed by simple expansion of isolated components. We need to consider a more conceptual approach to handling risk in general that can adapt and evolve as both the underlying systems and business objectives alter.
This allows organizations to move to a more dynamic and responsive architecture where static point-in-time verifications with long tails of low assurance are replaced with specific and targeted controls.
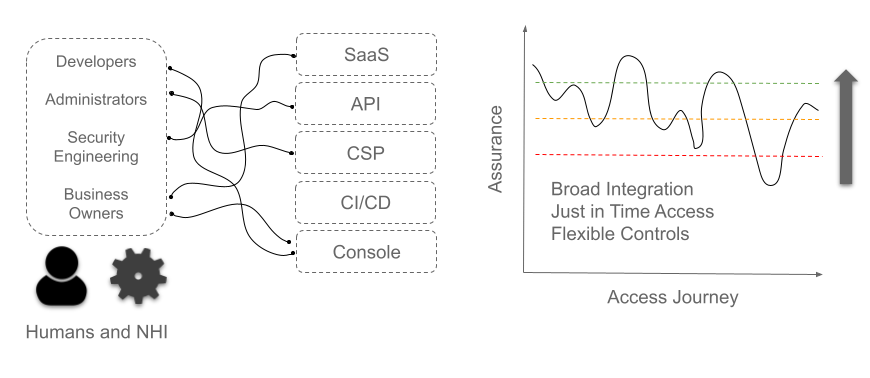
Risk, of course, should be treated as a spectrum, and not all protected privileged resources will carry the same likelihood of attack or the same impact if attacked.
The rise in outsourced infrastructure components such as CSP-delivered storage, compute power and network components will have a different risk profile to a subscription SaaS application with basic delegated account administration. Both, however, should follow the same risk assessment concept and be integrated into a least privilege, just in time access control model, coupled with strong attribution.
➔ Different systems
➔ Different users
➔ Different metrics: MTTA
The expansion of resources that fall outside the standard employee workforce operating model is complicated further by the rise of “cloud”. Not all clouds, of course, are the same, but all introduce a varied and gradient-based approach to shared responsibility.
From a non-technical line manager adding or removing team member access to a pay-monthly SaaS, through to developers and infrastructure operations teams using APIs to access a cloud service provider control plane. The types of integration will vary, requiring a broader approach to system integration that covers a range of API, web, human and non-human protocols and flows.
The increased variety in the deployment ecosystem has created non-technical challenges too. Yes, we have more and different identities to manage, along with different protocols and system connectivity requirements, but we also have different stakeholder success metrics to support. Whether you are a traditional infrastructure administrator or a microservices software engineer, your pain points, incentives and metrics will be different.
Traditionally PAM has been focused on applying controls and barriers to access. Slowing down adversarial activity through step-up authentication, segmented access, monitoring and lockout capabilities were expected. And because the number of users and resources was limited, the impact of poor user experience or slow access request fulfillment often went unnoticed.
Today, however, the impact cascades across teams, functions and objectives. Any barrier to adversarial activity must not in turn interfere with employee productivity, whether that is developer access, engineering deployment or security operations. Whilst standard cyber metrics such as mean time to detection (MTTD) and mean time to recovery (MTTR) are useful tools in measuring security controls, another angle to consider is the mean time to access: MTTA.
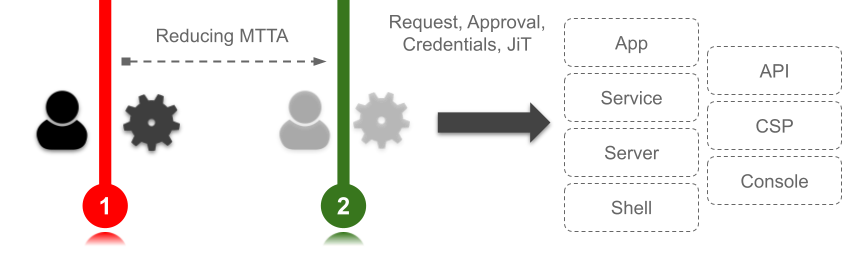
Here we move into the realm of removing barriers to employee access requests, access fulfillment, credential issuance and privilege checkout. Traditionally this has been focused on the standard user onboarding process, accelerating their ability to get working as quickly as possible. Basic rule-based access and linking identities to roles and groups using things like business units and job codes became standard design due to the measurable impact on employee productivity.
This core problem has not been solved; it has increased in scope due to the different personas requiring access to a broader range of resources. We need to include efficiency optimization for access request, credential issuance and just in time processing, not just for standard users but for services, humans, engineers and developers too.
This productivity improvement has a two-fold return. Initially, individual workload reduces and developers and engineers can focus on what they are paid to do: namely build applications, deploy code and configure infrastructure. Strategically, secondary benefits such as faster time to deploy new compute, storage and applications have significant business implications. An extension to this is the speed and efficiency of being able to alter service deployment during the response and recovery stages of an outage, whether cyber related or general failure.
➔ Decoupling AuthX
➔ Privileged access future proofing
The ability to collapse the gap between privileged resources and inbound identities with just in time processing allows us to move to a “zero touch” way of requesting and fulfilling access management.
Similar to external authorization management platforms a decade ago, the movement to central policy-based access control for standard web access management freed up resources within applications by allowing a centralized specialist tool to handle policy and logic. That design pattern moved standard authorization to be a business enabler with consistent enforcement, reusable policy components and improved security visibility. This allowed businesses to share more, with more people, faster and more securely.
The same concept applied to more privileged systems opens up a repeatable and consistent way for privileged humans and non-humans to gain access to a broad array of resources. By decoupling and centralising policy, a standard pattern emerges that allows organisations to continually add to the pool of high-risk privileged resources without the need for system-specific and proprietary controls, instead moving to an identity-centric approach with limited uplift when new high-risk systems, infrastructure and protocols are added.
The net result is improved developer and engineer productivity and security assurance, which by design allows the business to rapidly deploy more to more environments.
If you're struggling with the tradeoff between strong security and developer agility, P0 has developed a practical guide to implementing Just-in-Time (JIT) access available here.
Simon Moffatt has nearly 25 years’ experience in IAM, cyber and identity security. He is founder of The Cyber Hut - a specialist research and advisory firm based out of the UK. He is author of CIAM Design Fundamentals and IAM at 2035: A Future Guide to Identity Security. He is a Fellow of the Chartered Institute of Information Security, a regular keynote speaker and a strategic advisor to entities in the public and private sectors.
Get a demo of P0 Security, the next-gen PAM platform built for every identity.