P0 manages the entire privilege lifecycle for users, workloads and agents to programmatically replace standing access with least-privilege, short-lived and auditable production control
Legacy access workflows are tied up in vaults, static credentials and jump-hosts
Enterprises are left grappling with a proliferation of static credentials, standing privileged access and a poor developer experience that disrupts workflows and delays access. Doing the best they can with break-glass accounts, static tokens, and countless over-permissioned users. This approach simply does not meet the scale and flexibility required by the modern enterprise.




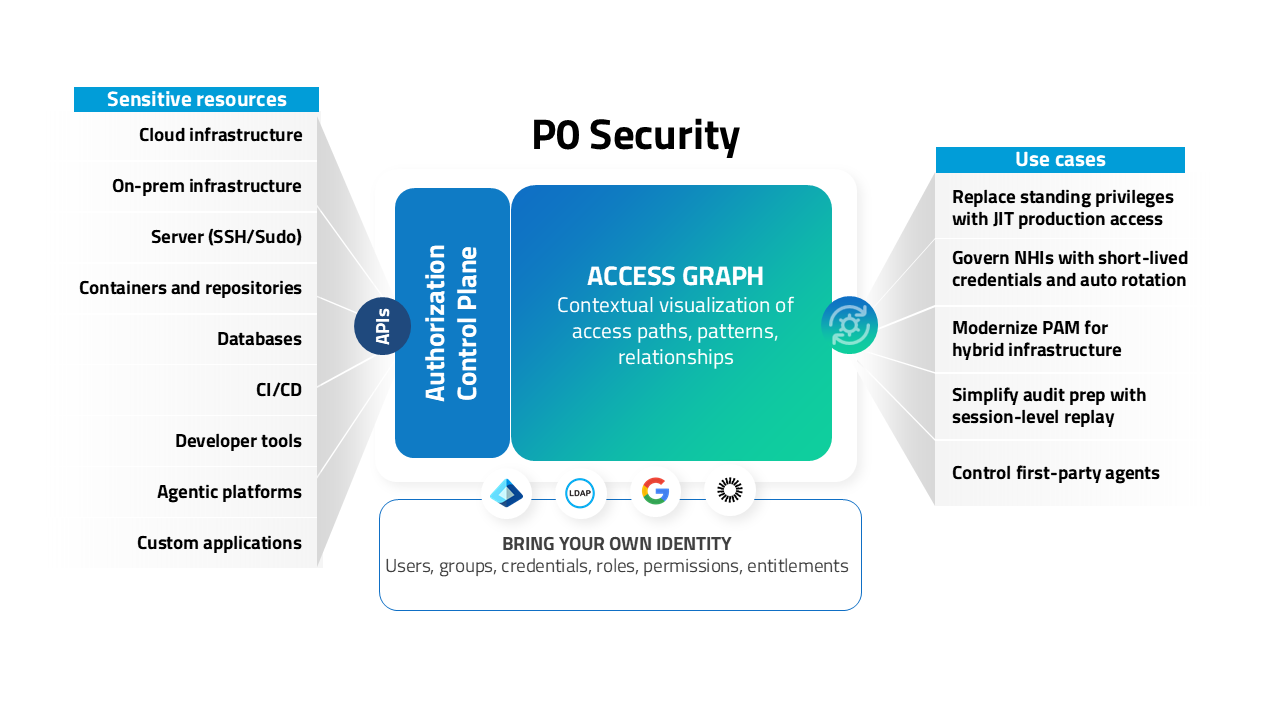
P0 Security manages the entire privilege lifecycle to programmatically replace standing privilege with least-privilege, short-lived and auditable production access. The P0 Authorization Control Plane delivers centralized access automations with just-enough-privilege and just-in-time controls to power ZSP at scale.
Our mission is to ensure zero standing privileges with zero access friction, because threats to your sensitive production resources are priority zero.
Bring your own identity, P0 will provision the access
P0’s “bring your own identity” methodology speaks simply to our focus on provisioning privileged access, rather than introducing secondary authentication layers beyond your existing IdPs that you already govern.
IdP-native authZ: Federated identities stay intact for complete visibility, granular audit logs and simplified operations
No shadow authN: Eliminate static credentials, shared accounts, costly infrastructure and needless user friction
P0’s identity-native architecture pulls all access related metadata across users, NHIs, and agents into a single source of truth. Delivering comprehensive context for determining what’s privileged across the entire production stack, from code repositories to databases and from multi-cloud to on prem.

Grant the right access at the right time with policy-based access controls enforced natively at runtime via APIs.


Inform and enforce closed-loop zero standing privilege programs that shrink your identity attack surface and simplify compliance for stringent regulatory requirements such as SOC2, GDPR and NIST.
Enforce consistent governance and streamline access workflows across cloud and hybrid environments.

See for yourself how P0 Security is redefining PAM.
An access graph maps relationships between users, roles, service accounts, policies and permissions across your environment — providing full-context visibility into who can access what.
P0 automates the full access lifecycle — including JIT access, approvals, credential rotation and expiration — with no agents or tickets, using tools like Slack, CLI and JIRA.
Legacy approaches to PAM have been burdened by static controls, vault-centric proxies, and brittle connectors that create standing privilege and high friction. P0 eliminates this complexity with centralized, policy-driven just-in-time (JIT) access controls.