Credential rotation shouldn't feel like a fire drill. In this episode of the Five minutes to zero standing access video series, see how P0 automates the entire credential lifecycle—coordinating rotation, notification, and safe handoff.
Watch a real example with GCP service accounts, Secret Manager, and Jira integration to see how P0 ensures secrets stay fresh without disrupting production.
Most security teams agree: credentials should be rotated frequently. But ask how often it actually happens - across service accounts, automation keys, and cloud access tokens - and you’ll hear a different story.
Rotations get postponed. Owners are hard to track down. Tickets pile up. Vaults go out of sync. And somewhere along the line, a service fails silently because an old credential was disabled before a dependent system was updated.
This isn’t a tooling problem. It’s a coordination problem.
And it’s exactly the kind of problem P0 was built to solve.
Credential rotation sounds simple: replace a key, update dependencies, revoke the old one.
But in reality, most workflows break down because the responsibility is fragmented. No one owns the full lifecycle. Secrets get rotated without warning. Vaults and ticketing systems don’t talk to each other. And when there’s a failure, the root cause is often buried inside a forgotten Jira ticket or a disabled key that still powered a production dependency.
That’s why most teams silently defer rotation - or worse, rotate credentials manually and hope for the best.
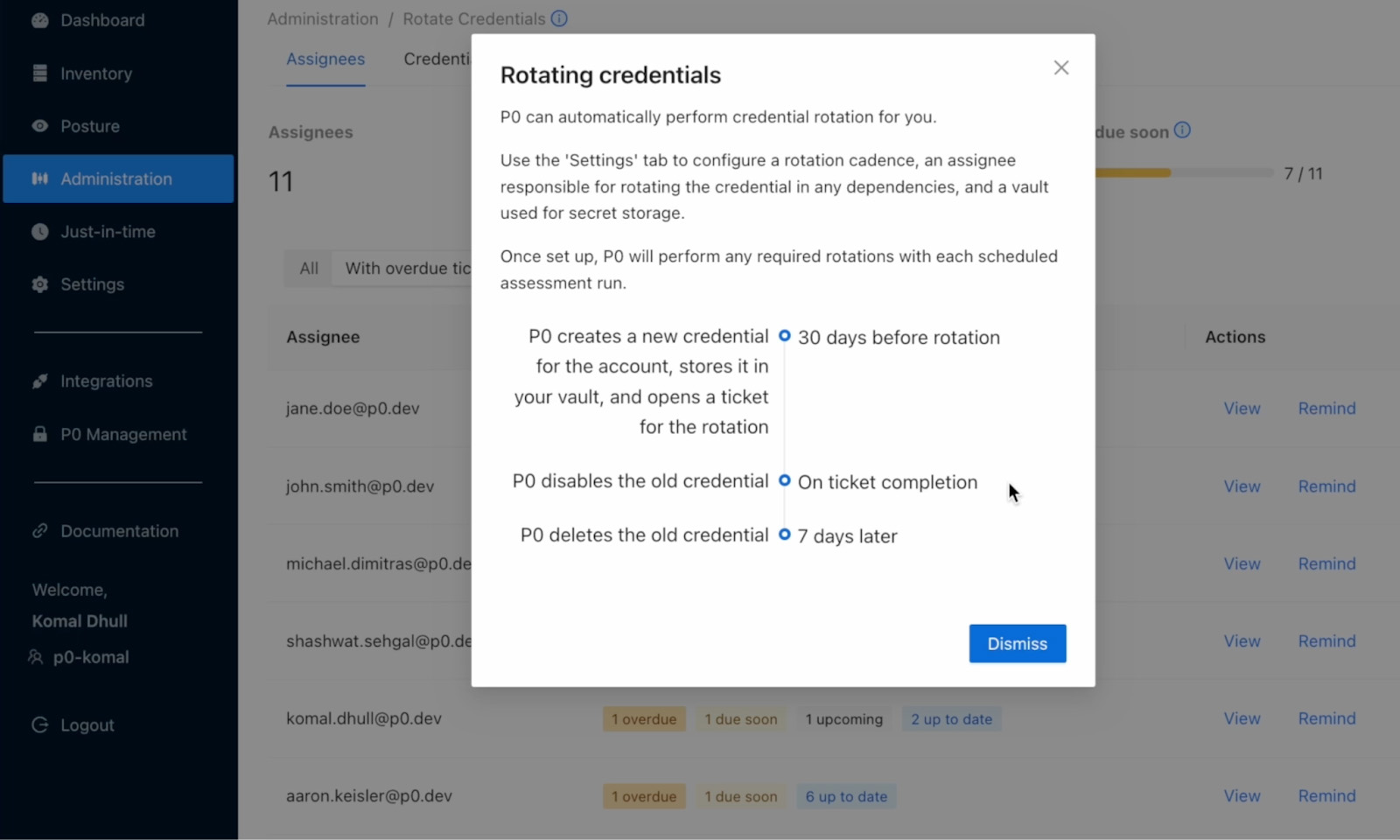
In this how-to video, we show how P0 automates the full lifecycle of credential rotation - without skipping critical coordination steps.
The demo covers how to:
In the video, we follow a rotation from start to finish:
Let’s say you want to rotate a GCP service account key every 90 days. With P0, you don’t need to script this out manually or rely on someone remembering to trigger a job. You simply define three things: the vault where the secret lives, how often to rotate it, and who’s responsible for updating anything that depends on it.
From there, P0 handles the rest:
No manual cleanup. No guesswork. No risk of premature breakage.
The magic isn’t just in automating the vault action - it’s in coordinating the entire lifecycle across teams and tools.
P0 treats credential rotation as a governance workflow, not a one-off automation job.
You get:
Rotating credentials shouldn’t be a fire drill or a manual checklist.
With P0, it becomes a structured, repeatable flow:
Credential rotation moves from “eventually” to automatic. From risky to reliable.
If rotating credentials still feels like a gamble - or worse, an afterthought - this walkthrough shows how to fix it for good.
Get a demo of P0 Security, the next-gen PAM platform built for every identity.