This episode of the Five minutes to zero standing access series walks through a modern way to grant and revoke admin access to Grafana—using Okta groups and just-in-time controls.
See how P0 dynamically updates group membership at login, ensures access is short-lived, and eliminates manual cleanup. Perfect for teams managing sensitive dashboards.
Granting admin access to Grafana is easy. Revoking it on time? That’s where most teams fall short.
When access is tied to static group membership in Okta or another IdP, there’s no easy way to say “just give this person admin access for 30 minutes.” So access sticks around. Privileges linger. And there’s no system enforcing the boundary.
In this short demo, you’ll see how P0 makes that boundary enforceable — without changing your identity architecture.
We walk through how to use P0’s just-in-time access provisioning to grant temporary Grafana access by dynamically inserting a user into the correct Okta group - the one that controls their Grafana role.
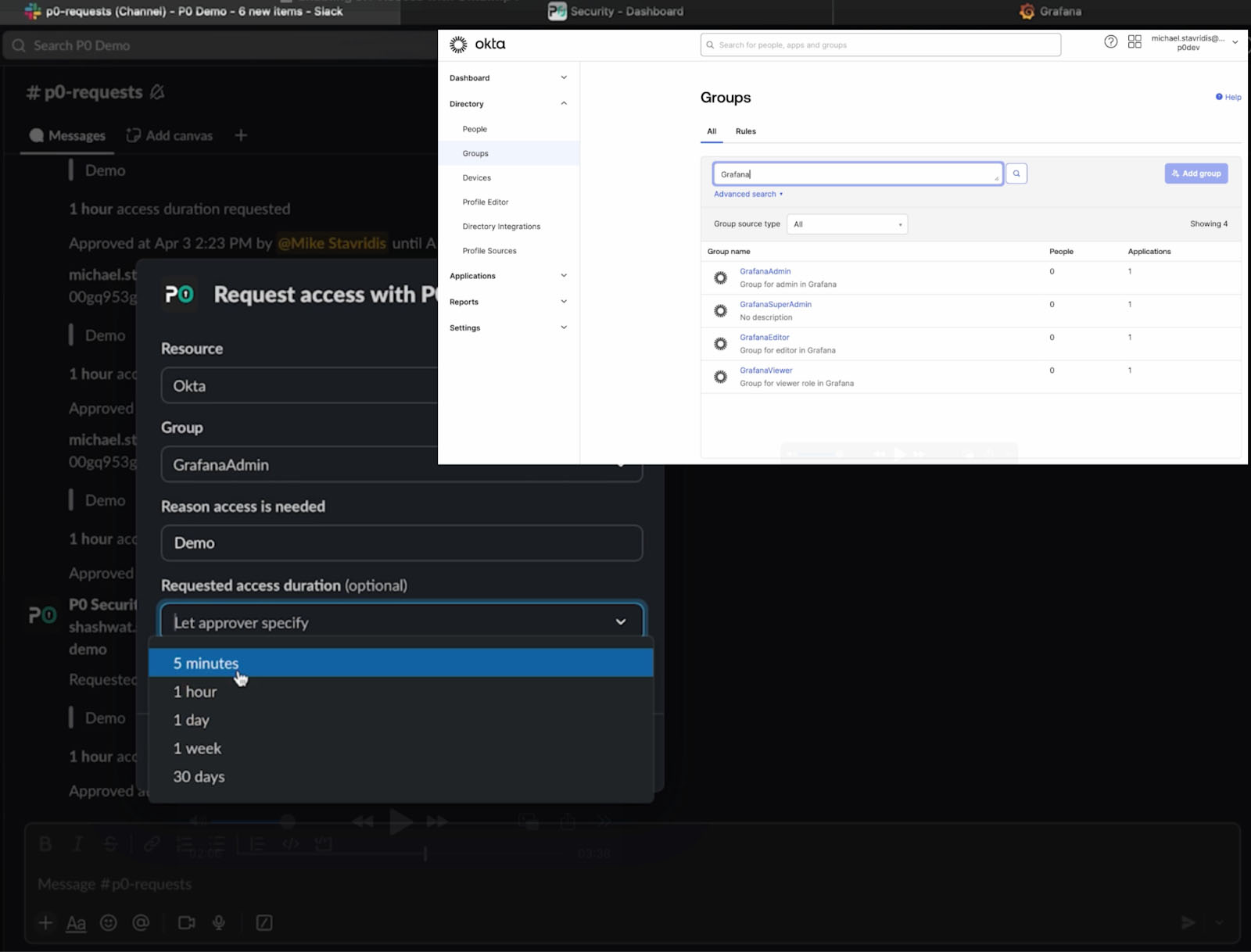
Grafana maps user roles using Okta group claims during login. In this setup:
The user initially tries to log in to Grafana via Okta but is denied - they aren’t in any Grafana group.
They then submit a JIT access request in Slack via the P0 bot. For demo purposes, self-approval is enabled. Once the request is approved, P0 temporarily adds them to the correct Okta group.
The user retries the login and is granted Admin access - all scoped, time-bound, and logged.
Once the access window ends, P0 (or an Okta workflow) removes the user from the group. That prevents re-authentication with elevated privileges.
If logout workflows are also configured, the active Grafana session ends immediately. Otherwise, users are removed at next login - enforcing least privilege even if someone forgets to sign out.
Critical apps like Grafana contain important or sensitive information. Granting or providing permanent admin access is low-friction - but it creates high-impact risks.
P0 brings discipline to that access model:
If you’re still managing access to critical apps through static Okta groups or hoping people remember to remove roles later, this demo shows you the safer, faster way.
Get a demo of P0 Security, the next-gen PAM platform built for every identity.