Check out this episode of the Five minutes to zero standing access video series to see how fast and secure AWS access can be—when approvals happen right inside Microsoft Teams.
Learn how to configure just-in-time access workflows using the P0 bot, route approvals to the right team members, and automatically revoke cloud access after it’s no longer needed.
In most organizations, temporary access to production environments is anything but temporary.
A developer files a ticket to debug an issue. The request sits in a queue. Hours pass. Access is eventually approved - often with broader privileges than necessary. And once granted, the access lingers. No clear audit trail. No expiration. No accountability.
When just-in-time (JIT) access becomes a ticketing problem, over-permissioned environments become the norm - and identity risk compounds silently.
On paper, temporary access should be easy:
A user asks for access, someone approves, and the system revokes it when time’s up.
But in practice, most JIT flows fail under pressure:
This leaves security teams enforcing access through processes, not systems. And it leaves access hanging long after it’s needed.
In this short clip, we show how to fix all of that - with P0’s MS Teams integration.
You’ll learn how to:
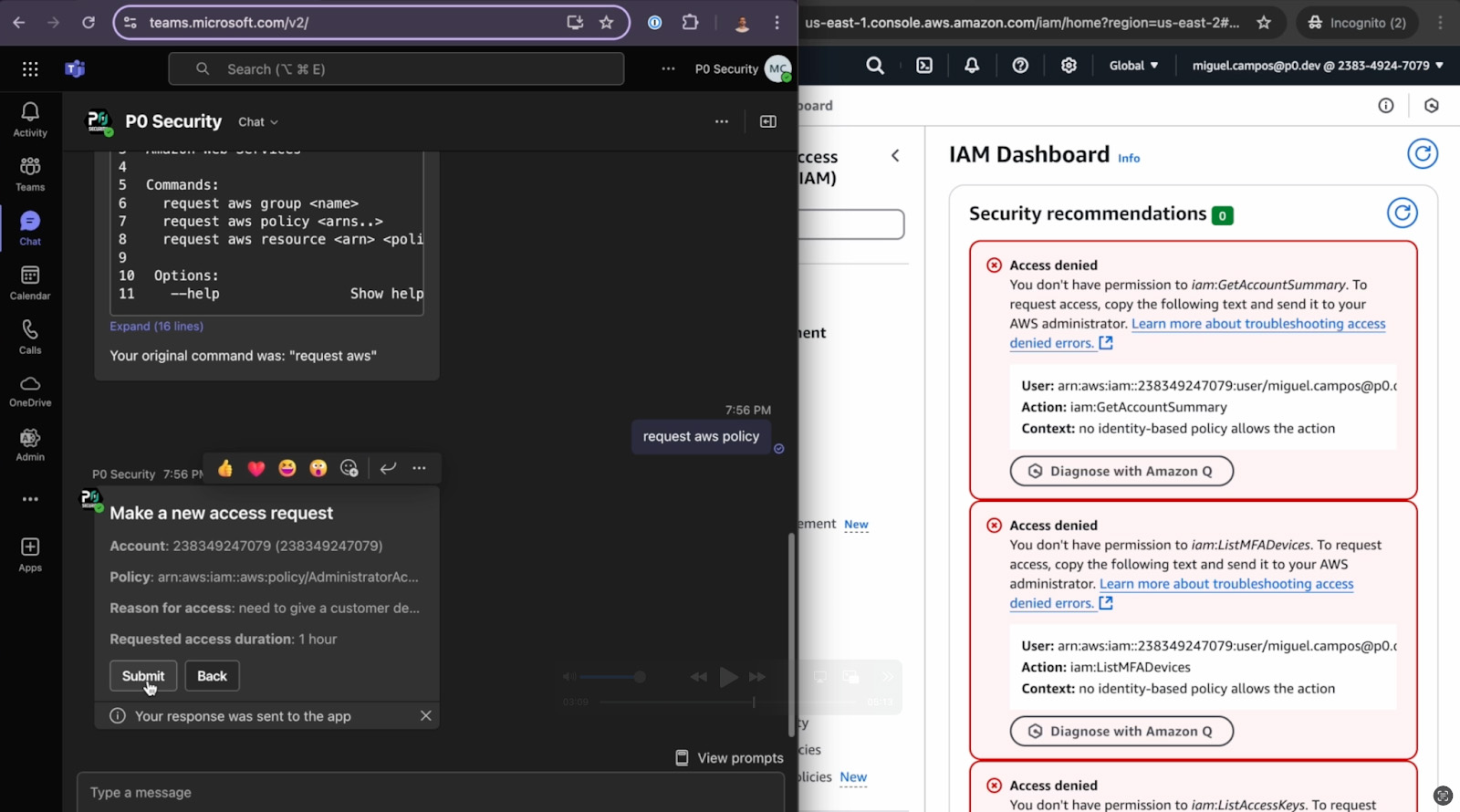
After setup, users interact with the P0 bot directly in Microsoft Teams. A simple command - like request AWS policy - opens a structured form where they specify what they need, why, and for how long.
Approvers receive a real-time notification in the configured Teams channel. They can approve or deny access with a single click, and they can set the access duration - whether 15 minutes or 4 hours.
Once approved, access is granted live. In the video, we see the IAM and S3 “access denied” errors vanish as soon as the policy takes effect. Users can now explore what they need - with only the privileges they’ve been granted, for only the time they’ve been approved.
And when the task is done? Access can be revoked immediately via the bot - or expires automatically when the approved duration runs out.
Everything is visible in P0’s governance console. Everything is auditable.
Most teams think they have JIT access under control - but what they really have is a fragmented mix of ticketing systems, tribal knowledge, and blind trust.
P0 replaces that with a secure, scalable, system-enforced flow:
No browser plugins. No custom scripts. No Excel-based reviews.
Just fast, governed access - from request to revocation - inside the tools your teams already use.
If you’re tired of ticket-driven access, or worried about how much access is lingering in AWS, this video shows what a safer, smoother workflow looks like.
Get a demo of P0 Security, the next-gen PAM platform built for every identity.