Got internal tools with admin panels tied to static Okta groups? You're not alone—and this episode of the Five minutes to zero standing access series shows how to modernize that model.
See how a lightweight integration lets you grant just-in-time admin access to homegrown apps—without rewriting your access control layer.
Most organizations have internal tools that weren’t designed with modern access governance in mind - lightweight dashboards, admin panels, or homegrown portals that rely on a simple “isAdmin” flag or hardcoded roles.
These tools often get left behind in access reviews. And because they’re internal, they tend to stay wide open - or worse, permanently assigned to privileged groups in Okta.
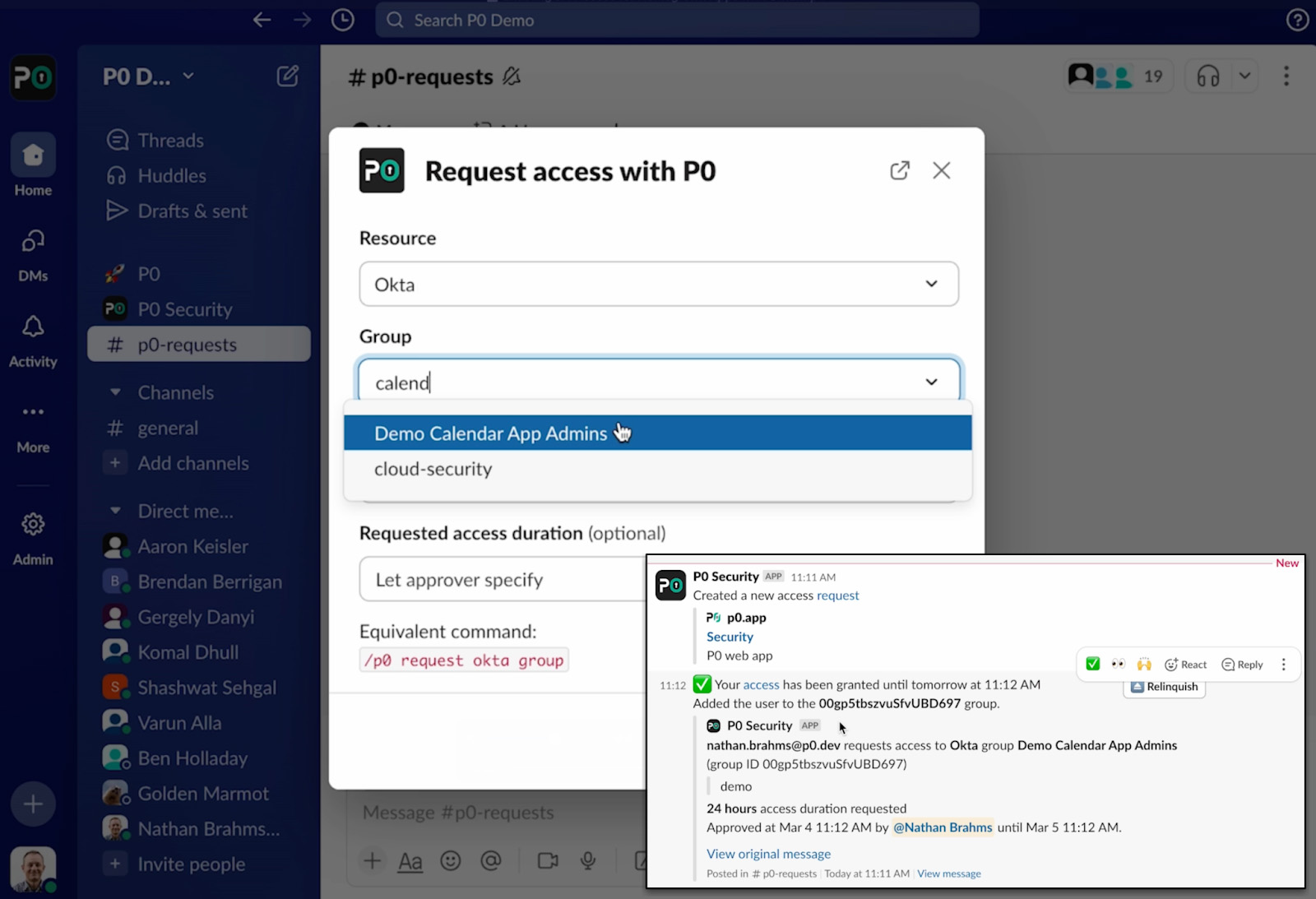
With a few lines of code and a lightweight integration, P0 makes it easy to bring these apps into your identity perimeter. In this demo, you’ll see how to enable just-in-time group-based access elevation for an internal calendar application - using Okta, OIDC, and P0.
It’s not unusual for internal apps to rely on something like:
if user.group == 'admins': showAdminPanel()
The problem? Most identity providers don’t make it easy to temporarily add a user to that group. Once someone is in, they often stay in. There’s no native mechanism to grant elevated access for 10 minutes or just for this one task.
That’s how low-stakes admin panels become high-stakes security risks.
This walkthrough demonstrates how to:
The internal app in this demo is a simple calendar tool protected by Okta SSO via OIDC. By default, a user logs in and lands as a standard user.
Here’s how the elevation process works:
This model doesn’t require rewriting your app’s entire access control layer.
It works with how most internal apps are already built — and how Okta already issues group-based identity.
With just a few lines of code, you can:
It’s an elegant, lightweight way to bring strong access governance to internal systems - without rebuilding your infrastructure.
Once the user relinquishes access (or it times out), P0 removes them from the group. The next time they log in, the group claim is no longer present in the token - and the app renders the standard user experience again.
There’s no need to manually revoke roles. No lingering admin access. Just-in-time, in every sense of the term.
If you’ve ever struggled with managing elevated access in homegrown apps, this demo shows how a simple integration and a Slack workflow can bring control, transparency, and automation - without slowing teams down.
Get a demo of P0 Security, the next-gen PAM platform built for every identity.