If your on-prem access model still relies on static SSH keys and jump boxes, this video is for you.
This episode of the Five minutes to zero standing access series demonstrates how to bring just-in-time SSH to bare-metal environments—using short-lived certificates, Slack approvals, and session-level revocation.
Most identity and access tools stop at the cloud boundary. But the reality for many organizations is hybrid: VMs, containers, and yes - still some bare-metal machines that run critical services.
In this short demo, you’ll see how P0 makes it easy to enable temporary, certificate-based SSH access to on-prem machines, without hardcoded keys, long-lived users, or manual ticketing.
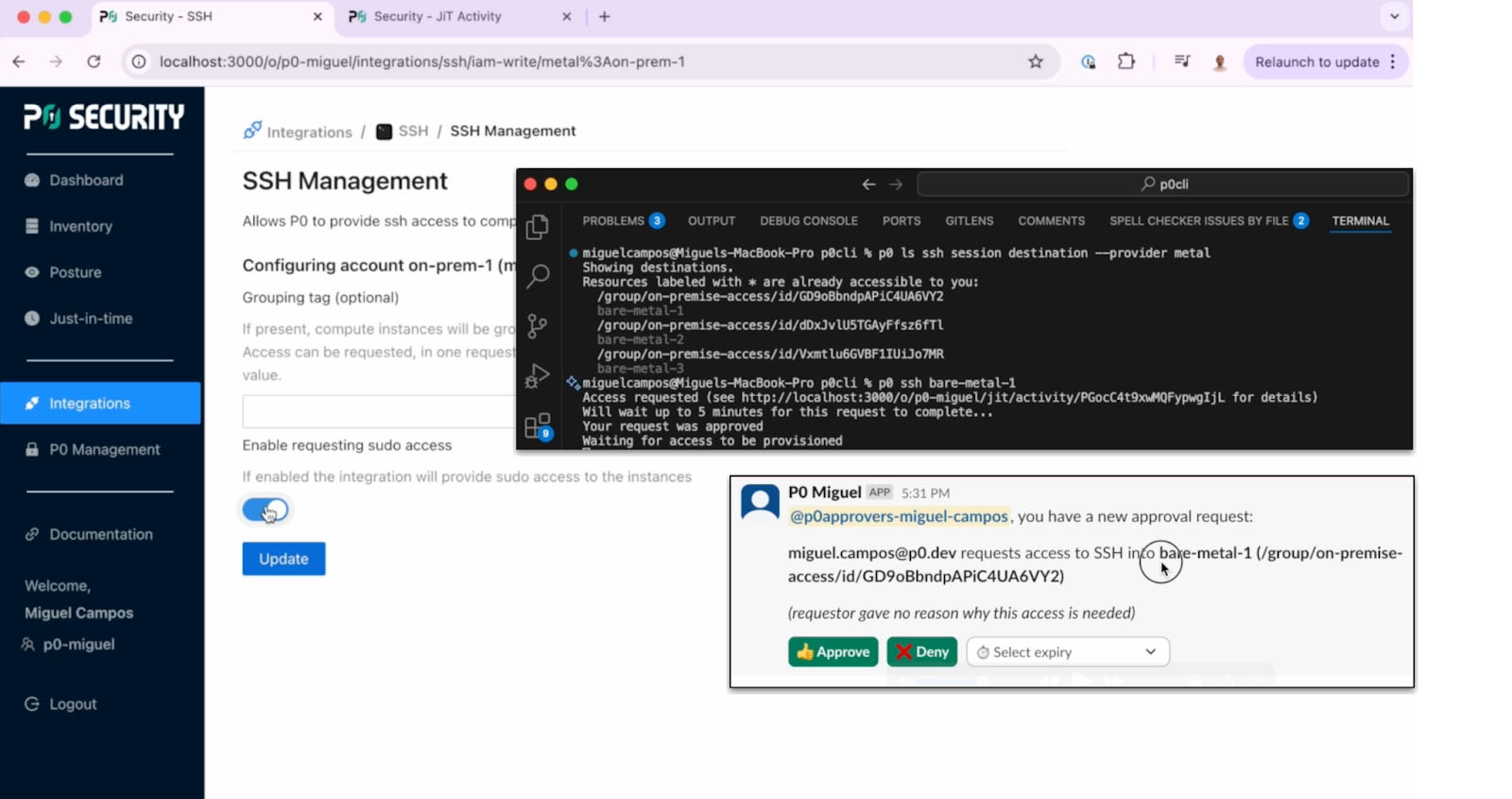
The user authenticates via Okta and logs in through the P0 CLI. Using p0 ls, they view a list of available nodes, filtering down to on-prem machines with the --provider metal flag.
From there, they run p0 ssh. Behind the scenes:
On-prem systems are often governed by legacy controls — static keys, persistent local users, and outdated jump boxes.
P0 replaces that with:
If you’re still managing on-prem SSH access with static keys or shared users, this demo shows how to bring least privilege and automation to bare-metal systems.
Get a demo of P0 Security, the next-gen PAM platform built for every identity.