The Principle of Least Privilege (PoLP) is a critical security concept for modern public cloud security. It implies that all identities (both human and non-human) only enjoy the bare minimum access required to perform their tasks. Additionally, PoLP states that access should only be granted for the duration necessary to complete said tasks.
Despite least privilege being a keystone concept of modern cloud security, companies find it hard to implement.
PoLP is a challenge for older organizations that have evolved from simplistic legacy systems where access was all or nothing - you either had access to a resource or you didn’t. And the security environment wasn’t nearly as complex as it is now with cloud and multi-cloud environments.
And startups struggle with PoLP even when they are cloud-native because they over-provision developers initially to support productivity. Narrowing down permissions and privileges later leads to pushback from developers. Growth stage startups earn their revenue from developers pushing code fast, so the risk of hampered productivity deters them from enforcing least privilege sooner.
On top of organizational challenges, there are the increasing complexities of cloud environments. Every resource in the cloud today has multiple policies associated with it and multiple ways to apply those policies to make it available to human and non-human identities (NHIs).
Then, you’ve got the identity provider layer outside of the cloud. People who are used to legacy systems will often bypass the cloud and execute operations at the identity provider level. You, as the admin, may find yourself enabling standing privileges because people want to get their work done quickly.
Non-compliance with PoLP doesn’t immediately manifest into a cyber incident. But it means you’re leaving yourself open to vulnerabilities. For instance, users may be able to execute tasks they shouldn’t be able to, like delete production database tables, disrupt customer SaaS applications, access sensitive data, etc.
Users may be able to access systems after they leave your organization, such as when identities aren’t cleaned up as part of the offboarding process. Or, if someone with malicious intent assumes an over-privileged role or identity, they could launch ransomware and phishing attacks, resulting in financial loss, reputational damage, regulatory compliance violations, and legal implications for you. There have been many incidents where poor access management gave cybercriminals leverage to increase the blast radius.
Take the Uber breach from September 2022, where hackers gained admin credentials to access Uber’s Privileged Access Management (PAM).
We’re in the timeline where the annual average cost of cybercrime is set to hit $23 trillion by 2027, and when compromised identities account for a third of security incidents, companies can’t afford to take Identity & Access Management (IAM) lightly.
Least privilege is one of IAM’s most critical concepts.
The first step is building an inventory of all identities- human and non-human- and roles, using either the tool your cloud vendor provides or a third-party SaaS tool.
In AWS, you can view Users and Roles inside IAM.
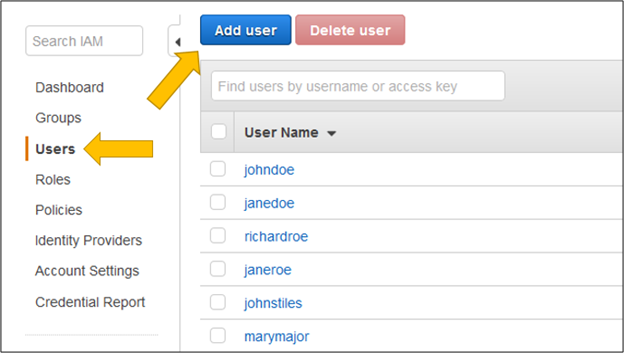
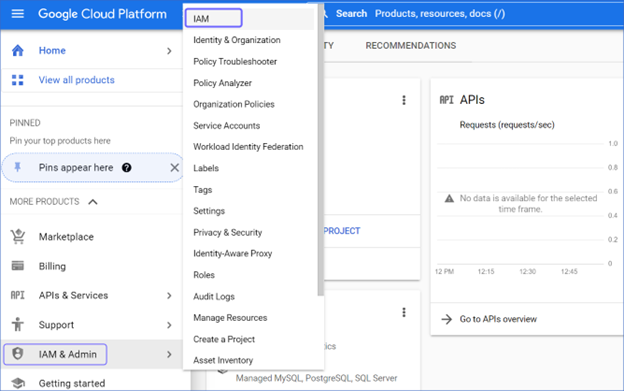
In GCP, navigate to the IAM & Admin section in the Google Cloud console,then explore the IAM and Service Accounts pages.
To view user roles:
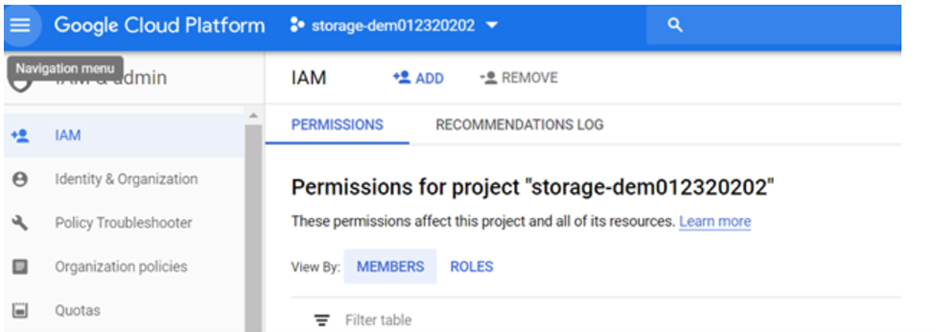
2. Select View by Members to list all members (users, groups, and service accounts).
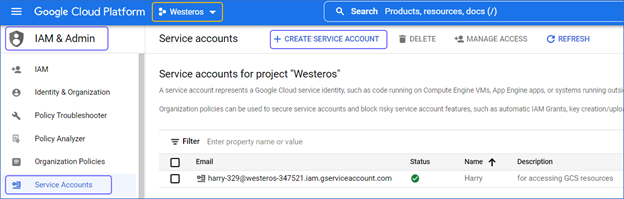
To view service accounts:
In Azure, navigate to Users under Manage to view all users.
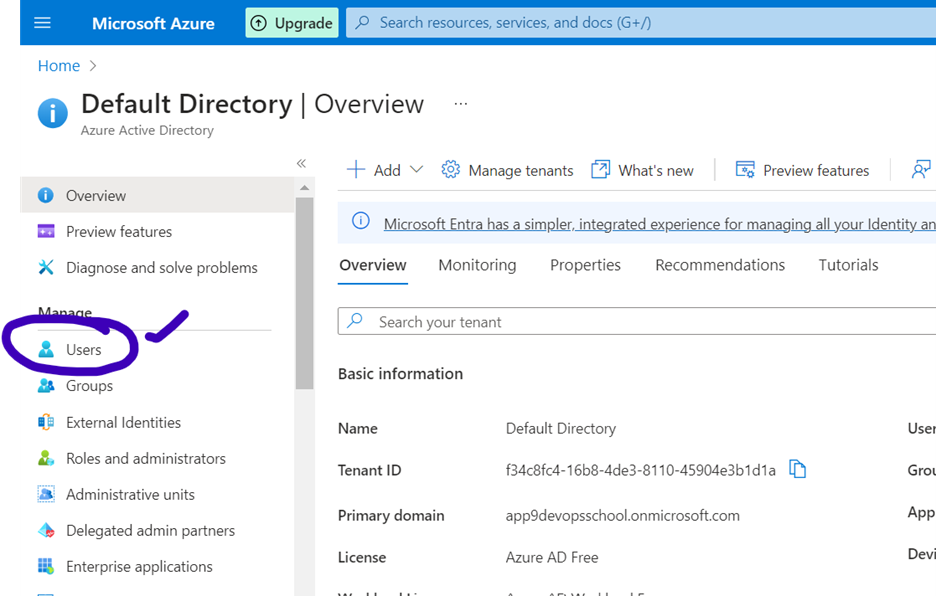
To view roles:
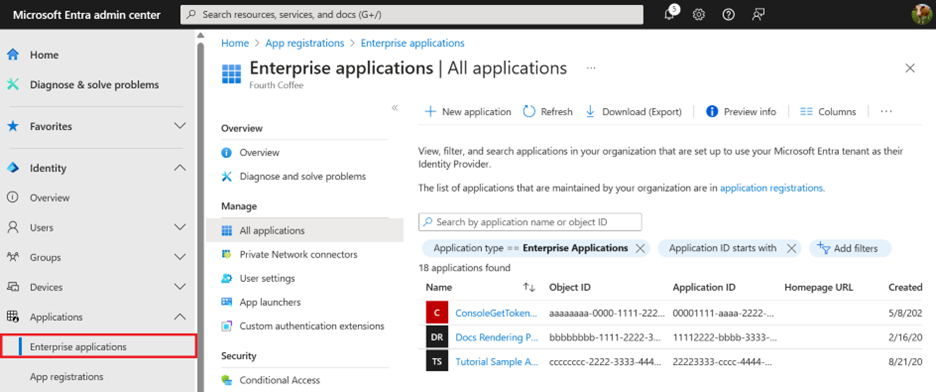
You’ll find service principals in Azure in the Enterprise applications page in the Microsoft Entra admin center.
Next, leverage an IAM policy analyzer or equivalent tool, depending on your cloud vendor, to find all unused and excess privileges.
One of our concerns is discovering permission sets that haven’t been used for over 90 days by their associated identity or role. Then, we can trim the permission set away as it is evidently not critical to that identity’s day-to-day tasks. Quarterly scans and audits can uncover unused permissions, so you can regularly cut down those policies, inching closer to least privilege.
In AWS, first create an analyzer for unused or excess privilege analysis.
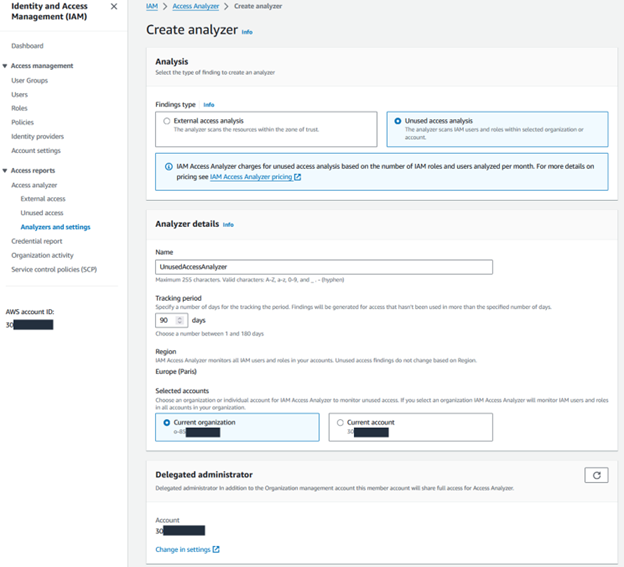
4. Your analyzer will aggregate and present its findings on a dashboard. Review the findings according to the finding type.
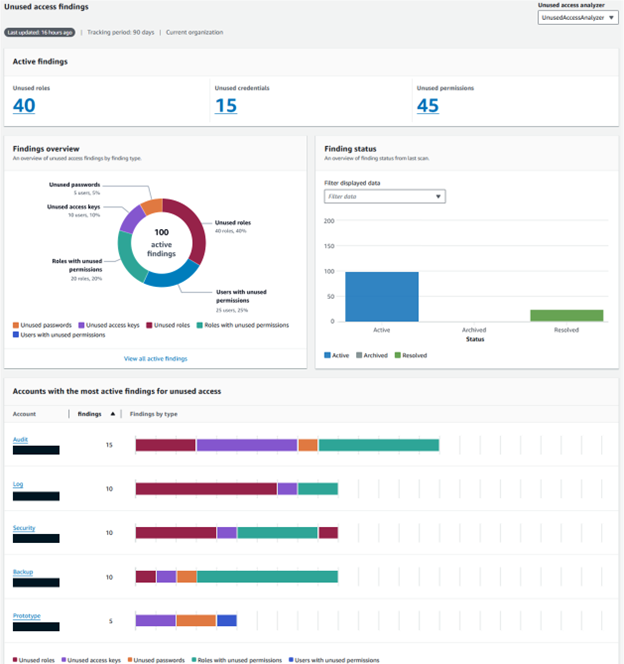
5. To specifically view unused permissions, set the filter on Findings type to Unused permissions on the list of unused access findings.
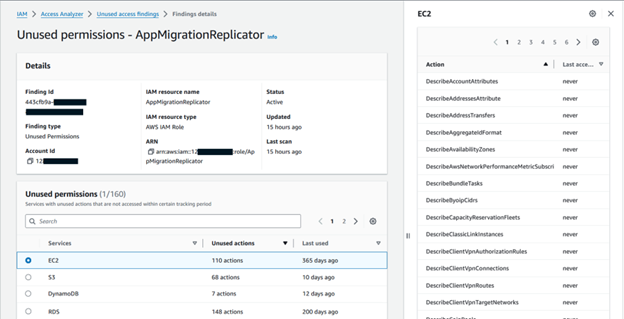
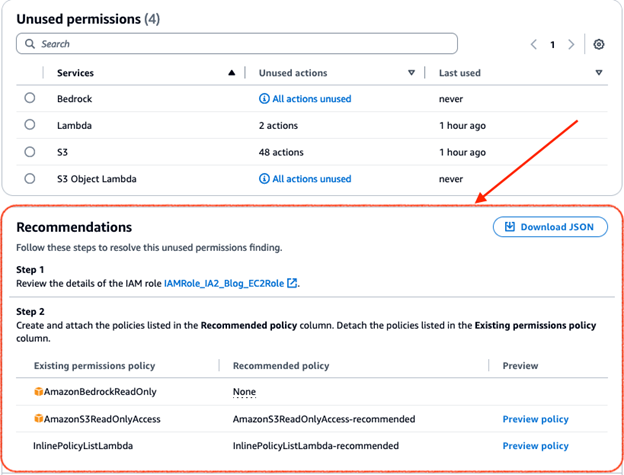
6. Use recommendations to resolve findings.
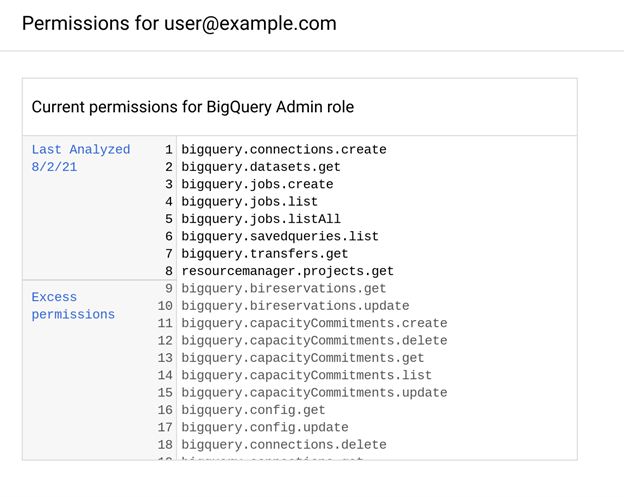
In GCP, navigate to the IAM & Admin section and select IAM.
In Azure, Microsoft Permissions Management can help you detect, right-size, and continuously monitor unused and excessive permissions.
Reminder for Microsoft Entra users: Permissions Management is retiring on October 1, 2025. Now’s the time to prepare. Learn more about how you can consolidate visibility, risk, governance and orchestration with a single cloud-native platform.
Follow these steps:
To view data, click on the Authorization Systems tab. The data collection process takes some time and occurs in 4-5 hour intervals.
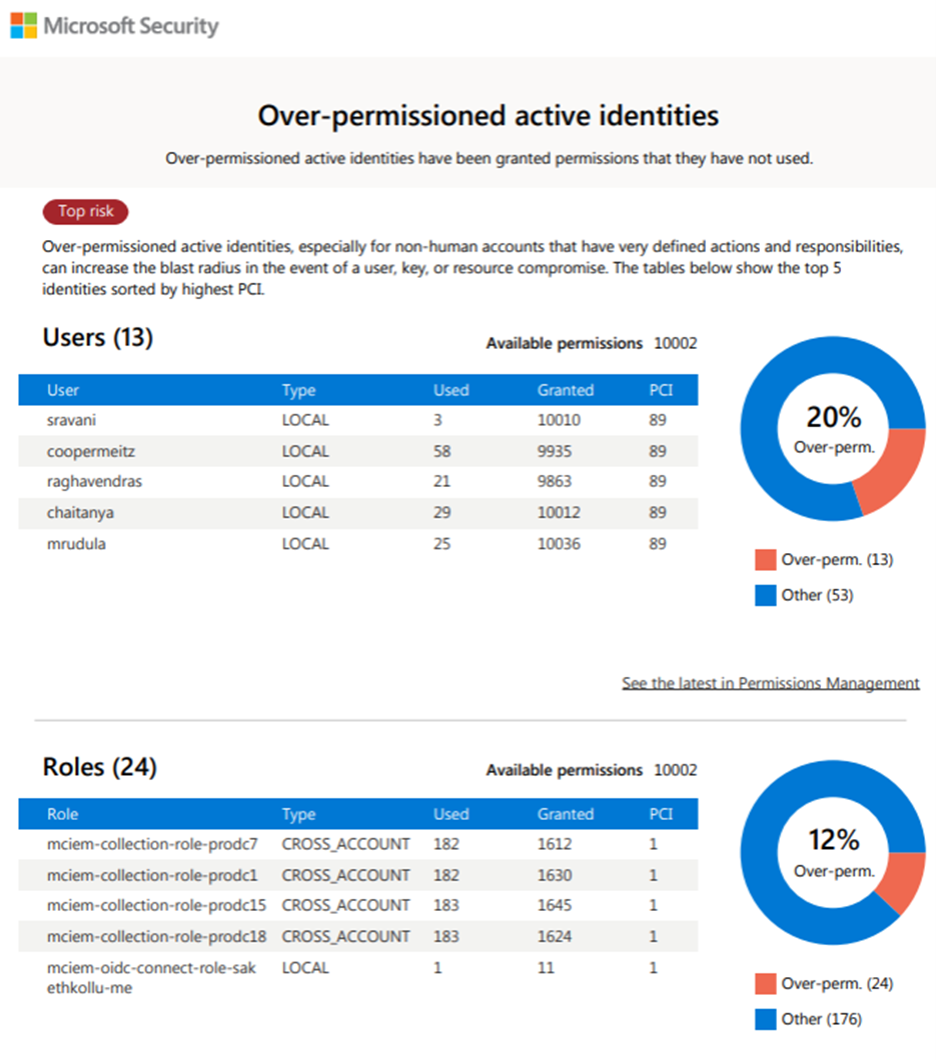
Next, combine and correlate trail logs from your cloud vendor with policy analyzer data to get a more accurate representation of your company’s risk posture.
We do this because policy analyzer APIs will sometimes throw ambiguous data your way, saying some of the permissions usage was unknown. So this correlation will better reveal exactly when each policy was last used.
Step 4: Enable dynamic permissioning with Just In Time (JIT)
Go a level higher with a just-in-time (JIT) tool. Microsoft Entra ID Privileged Identity Management (PIM) provides just-in-time access for admin roles in Azure, AWS offers Temporary Elevated Access Management (TEAM), and GCP has an open-source application called Just-in-Time Access.
Dynamic permissioning with JIT helps you move away from standing privileges so that when someone gets an invite to be a user in the cloud, they start with zero privileges. Then, the admin can pick and choose what permissions and roles each user assumes and for how long.
With a JIT tool, users say, “Hey, I need to do x amount of work for which I need these permissions - if those permissions come packaged up in a role or a permission set, I want to assume that role”. Once users get approved, the roles get attached to their identities, permissions get elevated, and they can do their work. Once their work is done, the permissions are retracted until they’re needed again.
That’s the holy grail of least privilege - and where you want to reach.
Learn how a leading insurance provider eliminated 30,000+ static keys, right-sized over-privileged access, and achieved full governance on NHIs within weeks of using P0 for their GCP cloud. Read the case study here.
Instead of having to go through disparate tools like policy analyzers, cloud trails and JIT tools, P0 allows you to achieve everything using one tool.
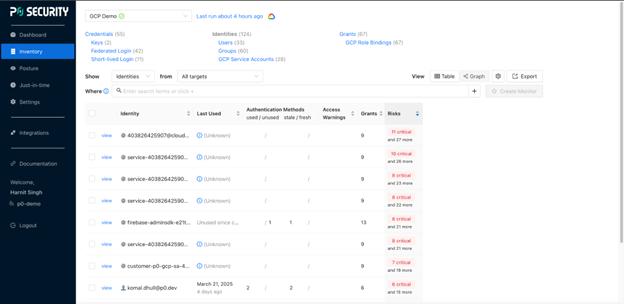
Here’s how the inventory looks.
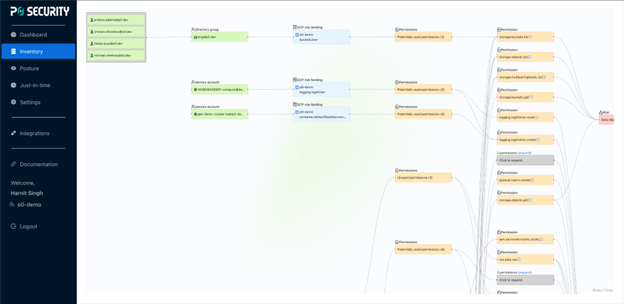
You can see your risk posture at a glance:
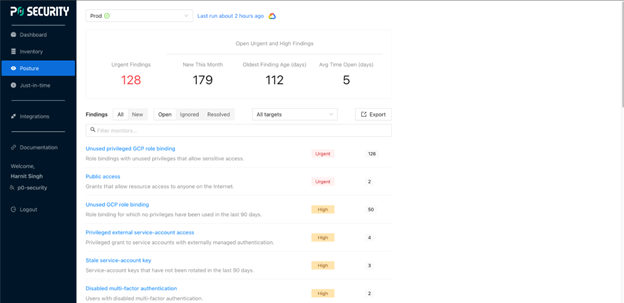
If you have unused or excess privileges, you get details of those findings. Then, P0 recommends commands to run to trim down the roles.
And, P0 also offers Just in Time permissioning.
P0 serves as the single interface to manage your public cloud security. While some tools focus on human entities and others on non-human entities, we will show all your cloud principals along with the resources they have access to, alongside their authentication history.
Sign up for P0 for free and conduct your first IAM assessment in less than 15 minutes.
Get a demo of P0 Security, the next-gen PAM platform built for every identity.