Why PAM Needs to Evolve
•
Oct 17, 2025
•
Oct 17, 2025
➔ Small and static set of accounts and functions
➔ Focus on roles, not behaviours
➔ Vaulting as main protection
Privileged Access Management (PAM) has been around commercially since the late 1990s, supporting a range of password vaulting and session management use cases for Unix based systems. The continual sharing of root and administration accounts not only became a productivity bottleneck it also introduced tangible risk to burgeoning security teams. External compliance initiatives often highlighted the need for improved accountability and traceability for the key management accounts used in many infrastructure and platforms teams.
These systems delivered focused and specific capabilities that often only needed to cover a small percentage of accounts and identities. The budget was typically released from the CIO and CISO communities with a limited set of users interacting with accounts under management.
Those initial platforms typically relied on “role” based association - be that looking at the server and web infrastructure teams for example, or perhaps mainframe and Unix administrator functions. The checking-out of an account, along with the associated password rotation and session monitoring was linked to a user assuming a set role for a limited period of time.
The number of accounts, associated identities and integrating systems was limited - all of which were under a near full-control of administrators due to being on-premises. Of course, the infrastructure needing protection, the deployment model and the threats that needed to be treated evolved in the following decade.
➔ More privileged identities
➔ Increase in systems needing integration
➔ The role of cloud computing
The rise of “cloud” brought some fundamental changes to how organizations both procured and managed core infrastructure services - think compute power and storage, then more laterally a huge array of secondary functions for operations, monitoring, network and more - as well asthe consumption of software-as-a-service applications. Run-operate costs sunk,but the risk was only altered, not removed. So suddenly each SaaS application would expose management interfaces and administrative functions that needed to be controlled.
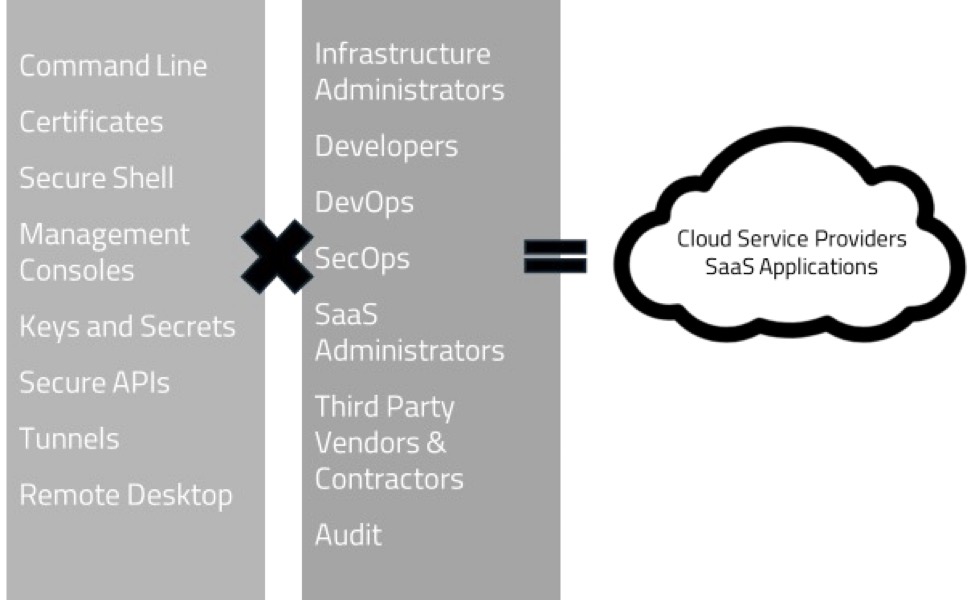
Access into cloud service provider (CSP) platforms was first done remotely across untrusted networks (enter the zero trust design pattern) as well using a broader array of protocols and access methods.
Command line interfaces, certificate-based possession factors, trusted client IP addresses and locations as well as bastion hosts all needed to be added into the mix. In addition to this,different stakeholders and people were emerging that needed access to these more high-risk environments.
Developers, developer operations, specific SaaS administrators and traditional audit and administration teams needed to manage both existing on-premises resources and a new array of cloud-related technologies. The volume of variety of both systems and identities requiring integration increased. This also generated new functional and non-functional requirements.
New protocols were required to connect to remote systems, improved security such as consistent inbound strong authentication and monitoring as well as broader adoption of policy-based access control became popular. This supported production-ready and scalable PAM platforms that could rapidly respond to changes in the type and volume of the systems and identities requiring access.
➔ Palo Alto Acquisition of CyberArk
➔ Change in requirements and success metrics
➔ Movement to ephemeral, dynamic and Just in Time for all
In recent years however, a scalable and policy-centric approach to privileged access management has become table stakes. We are now entering a new era with increasing reliance on cloud, but also upon ephemeral and dynamic models of access.
The recent acquisition of CyberArk by Palo Alto indicated a sea change in how organizations now see privileged access. Clearly an acquisition is heavily dependent on revenue and existing customer management,but it also showcases the current trend for increasing convergence between identity, privileged access and cyber security. Whilst in many organizations they have always been intrinsically linked, they do in fact have different metrics, budget holders and persona-engagement. As organizations now design identity-first security architectures that support zero trust, the privileged access aspect takes on greater importance. It can no longer be seen to hold back either employee productivity (in the case of devops), increase risk (due to poor deployment coverage) or be vulnerable to emerging exploits due to poor visibility.
Modern-PAM needs to support more systems, more accounts, a hybrid deployment landscape and have the functionality available to a broader array of integrating technologies via modular, composable and API-first capabilities.
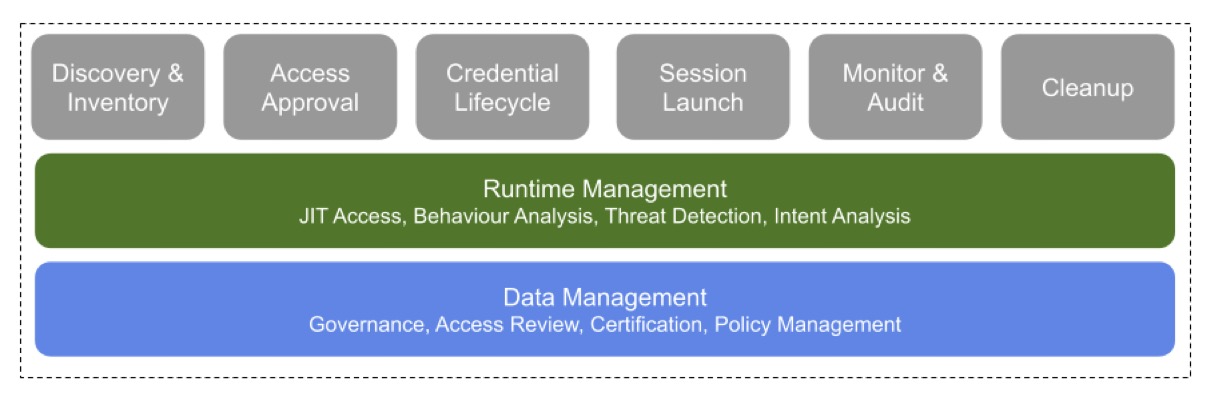
IT in general needs to “meet the business where it is” - and from a PAM point of view that entails ephemerality with respect to credentials, permissions and access grants. Business agility is an essential facet of delivering modern products and services and PAM-related capabilities should not be an inhibitor to its growth. Just-in-time access is now a common design pattern and must be implemented for all users, not just high-risk ones. From a PAM point of view we need to consider this from a lifecycle perspective, then in turn look at both the data layer and runtime behaviours.
The core PAM life cycle is typically well understood but it now needs to be deployed to more systems (and across more human and machine identities) in a more modular fashion. The emergence of infrastructure management tasks being handled “as code” demands DevOps and SecDevOps discovery and credential and key management workflows. Access approvals need to be simple to complete using modern chatops tools and mobile-ready interaction patterns. Runtime management needs to contend with complex intent analysis scenarios to help distinguish between classic “insider threat” or the simulation of insider threat by a complex state actor using a zero-day exploit.
These modern PAM requirements are needed today, especially with the rapid rise of AI-based systems with complex service and credential management use cases. Improvements to both the data aspect (permissions, policy and governance) as well as the post-access monitoring and audit should be both strategically deployed yet easily expanded as more systems require their capabilities.
Simon Moffatt has nearly 25 years experience in IAM, cyber and identity security. He is founder of The Cyber Hut- a specialist research and advisory firm based out of the UK. He is author of CIAM Design Fundamentals and IAM at 2035: A Future Guide to Identity Security. He is a Fellow of the Chartered Institute of Information Security, a regular keynote speaker and a strategic advisor to entities in the public and private sectors.
Get a demo of P0 Security, the next-gen PAM platform built for every identity.